- BHA FPX 4020 Assessment 1 Health Care Problem Analysis Proposal.
Health Care Problem Analysis Proposal
Patient data security is among the many issues repeated in the clinical field. This is a titanic worry since senseless patient data sharing could create problems inside an association (Chen & Benusa, 2017). It was picked since everybody working in the healthcare area, notwithstanding people who deal with these problems firsthand, is affected by the security of patient health data.
These loads may bring issues for patients and clinically prepared professionals (Chen & Benusa, 2017). Furthermore, this problem happens more often than it should; consequently, thought should be attracted to it, and strategies should not be firmly established to get it anywhere near working.
Measurement and Assessment of the Problem
The BHA FPX 4020 Assessment 1 Health Care Problem Analysis Proposal utilizes the HIPAA Opportunity Assessment to overview healthcare or patient data security. This tool has five stages to help guardians ensure that healthcare and patient data are not seriously compromised (Kruse et al., 2017). These five stages include:
• Recognizable proof of the dangers and risks in the partnership.
• See who or what the bet or risk is disrupted.
• Further assessment of dangers and reasonable advances are made
• Divulgences are recorded, and savvy progress is executed
• Results are inspected, and if fundamental, careful advances are rethought of the authentic responsibility of patient secret sets patient data not indistinct from analyzing information and metadata.
- HIPAA Security Rule Compliance
Individual healthcare data and clinical history of people are safeguarded by open standards and measures under the HIPAA Security Rule (Chiruvella & Guddati, 2021). It fans out the cutoff centers and fundamentals that control the fitting dispersal of such information, paying little notice to patient assent (Chiruvella & Guddati, 2021).
Treatment plans combine time for information support and destruction, information demolition rules and cycles, and a structure of the data that ought to be available to satisfy the essential undertakings, such as ceaseless care transport and surefire prerequisites (Chiruvella & Guddati, 2021).
Public and state rules are planned for documentation, and veritable commitments concerning holding patient information are picked. An office should ensure that physical and electronic records are disposed of in proportionality with government and state basics after a report has served its whole upkeep term (Chiruvella & Guddati, 2021). Paper records might be disposed of by obliterating and consuming them, while microfilm and laser plates can be squashed, and electronic information can be alluringly degaussed (Chiruvella & Guddati, 2021).
BHA FPX 4020 Assessment 1 Health Care Problem Analysis Proposal
The trading of patient information is likewise dependent upon unofficial rules. From a general point of view, the Security Rule oversees who approaches patient information, whether in an electronic, uncovered, or verbal plan (Chiruvella & Guddati, 2021). Acquainting private patient information with parties other than the patient and the professional proposes destruction, restraint, and policing (Chiruvella & Guddati, 2021).
- Data Security in Healthcare
In conditions like these, specialists should make some sensible split between their professional and moral requirements to stay aware of the law and offer splendid treatment to everybody, paying little mind to their conditions. Moral contemplations depend on the insistence, security, and system of patient healthcare data, and security breaches hurt the moral assessments of health data.
As per Kruse et al. (2017), right now, confirmation, diagram, and security stresses concerning patient health data are enormous issues and impediments to the degree that the execution of healthcare-related impels, for example, electronic health records (EHR). This source talks about the problem as it means to give security procedures and approaches to patient data security, like firewalls and encryption, radio dreary ID (RFID), and cloud.
Figuring antivirus software, early bet assessment programs, and the approach of the central data security officer. Hassan et al. (2017) see that data security culture impacts end-client consistency with data security controls, rules, procedures, and policies inside the organization. The assessment’s openings in improving reasonable data security, as well as the Managers Plan (ISMS) for empowering a culture of data security in healthcare affiliations, connects with the picked problem.
BHA FPX 4020 Assessment 1 Health Care Problem Analysis Proposal
The third definitive assessment is associated with patient data security. It incorporates escalating and detaching different patient data security calculations and procedures, such as client refusal and access control highlights (Sheikhtaheri & Kermani, 2019). The producers note the evident assessments’ benefits and checks. Peikari et al. (2018) directed assessment to pick the relationship between organizational and human points of view and patients’ viewpoints on flourishing, for example, patients’ impressions of staff security care planning, seeing, morals, physical and mechanical license, and trust in clinical offices.
This study associates with the evident problem as, taking into account the outcomes, clinical offices ought to conceptualize plans to work on patients’ point of view on these parts, which at last impact how secure they feel, likewise, filling a couple of openings related with patient health data the supervisors (Peikair et al., 2018).
George and Bhila (2019) state that patient security recognitions are fundamental. The assessment discusses patient data security as it looks at the stresses of guarding security and mystery in healthcare and different evaluations of its worth to the two people and society.
Any individual is prepared for security, especially concerning data about their health. Individuals could live independently as one, essential, and entirely guaranteed by the significance of safety (George & Bhila, 2019). The last assessment worked by Pack et al. (2017) included looking at how organizational policies and procedures pick how clients of data and Progress assets ought to act to avoid, see, and answer security problems in data structures. Taking this into account, it assists with the problem concerning structure-wide policies.
Benchmarks
Finally, patient data security remains a problem considering public information benchmarks. In general, 53% of the analysed foundations have rules and cycles starting around 2016 that could genuinely ruin or immediately see and address patient data security issues (Eat et al., n.d.). This is a problem since, as per the overview, 45% of firms had more than five security problems in the past two years (Eat et al., n.d.). This could be used as a standard to gauge how well the quality has gotten to a more raised level.
The information shows that there are superfluous security problems, and patient data is brought when an establishment has more key security procedures set up; properly, there would be fewer security problems in the relationship with first-in-class security procedures. This benchmark will stay under the public typical. Utilizing this data, the establishment can evaluate the benchmarks from when the change is driven. How many security breaches over a year will likely be a benchmark for progress?
Furthermore, execution markers related to patient data security, like security episodes (emphasized), access to the board, defense and proactive position, data sharing, and status level, will be used (Argaw et al., 2020).
Action Plan
Next is the readiness action plan advances toward completing the capstone healthcare problem analysis project.
- Select a point locale
- Structure problem verbalization
- Spread out targets and goals
- Portray result measures
- Perform library search
- Examine research articles
- Play out a making overview
- Evaluate disclosures
- Present results
- Propose frameworks
The subsequent action plan is isolated into five regions to choose the problem of patient information security.
1. Organizational Standards
a) Establishing policies and rules for adornment responsibilities and business contracts (Keshta & Odeh, 2021).< br//>b) Improving organizational deformities and finishing the encroachment (Keshta & Odeh, 2021). br/ />c) Agreements should be routinely investigated and engaged as required (Keshta & Odeh, 2021).
2. Administrative Safeguards
- Appointing a security officer to be committed to making and executing new security rules (Keshta & Odeh, 2021).
- Conducting an assessment of the coalition’s utilization of the security policies’ necessities
- Determine likely threats to e-PHI (electronic patient health information), then set up organizational countermeasures (Keshta & Odeh, 2021).
- Risk assessments will be completed every time there is an update or improvement in the security of patient information. This applies to any shifts made throughout the action plan’s direction.
- When signed up, specialists will receive retraining on calm information security to ensure they are knowledgeable about the standards and procedures (Keshta & Odeh, 2021).
3. Technical Safeguards
- To avoid hacking, all data should be mixed, and threats to malware software should be presented (Keshta & Odeh, 2021).
- Set up a few access levels. This will make it essential for unequivocal people to stay aware of different kinds of income and might be able to see express graph parts. Limit responsiveness to the workforce who are not on the chart. Individuals could access patient records and information they require using their passwords (Keshta & Odeh, 2021).
- Routine access changes ought to be made to authenticate that every client has the guarantee to access the patient records they currently require (Keshta & Odeh, 2021).
4. Physical Safeguards
- Alarm plans will be executed in any office where patient information may be the likely opportunity to destroy unfortunate access (Kruse et al., 2017).
- Screens will be given the objective that they are not agreeable to patients or staff until they unequivocally search it out.
- Establishing rules for authentic vehicle send-off, clearing, and using electronic media (Kruse et al., 2017).
- The crisis office’s circumstances regarding all computers inside will limit unapproved people from using the workspace.
5. Policies and Procedures
- Change the policies and procedures according to the situation and when new conditions arise. After the changes have been made, all laborers should be ready for the latest procedures (Moore & Frye, 2019). Furthermore, they should review the updates.
- Employees must know the establishment’s policies and procedures during onboarding.
- All policies and procedures should be recorded and rapidly available to all specialists (Moore & Frye, 2019).
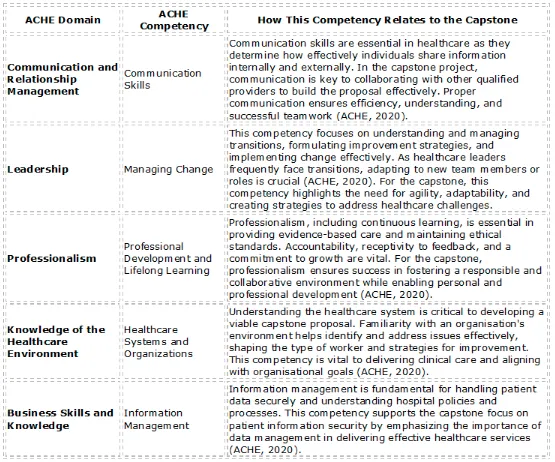
ACHE Leadership Competencies
Addendum
I contacted Dr. Mohammed Alnajjar, an MD who has filled in as an interior medicine specialist for the past 28 years, concerning my proposal. At this moment, he is working at El Paso Inside Cure Care. When I went through the proposal with him, he said the reality was astoundingly professional and raised extraordinarily authentic concerns concerning the standard standards and practices. He commented on how prominent the proposal was and how possible the action plan had the stores to join. He saw that different clinical establishments in the state-of-the-art world stand up to problems with patient/healthcare information security. We discussed how tremendous it is.
It is to keep the standards strengthened and rigidly executed so that patient information may be kept secure. He said that executing my proposal would improve both the chance of treatment and the flourishing of the patients. Since this issue impacts different healthcare affiliations and the healthcare system, if all else fails, it will be paramount, everything considered, to get everything moving on this cycle so we can refresh the foundation wherein we are used.
After finishing the study, he said and agreed that the proposal was perfect and that no updates should be made; regardless, he highlighted the importance of managing the policies, practices, and cycles enveloping the security of patient information. He embraced my proposed project, which satisfies the fundamentals of the association and the healthcare system, by and large, talking and unequivocally portraying the control of the execution of a data frame project.
Through a Skype meeting, Dr. Mohammed and I had a conversation on November 25, 2022, at 2:45 p.m. for nearly an hour (something like 50 minutes). This discussion was integral to developing the BHA FPX 4020 Assessment 1 Health Care Problem Analysis Proposal, which was carefully considered and settled after contemplating convenience, tendency, and time factor viewpoints. Signature: Dr. Mohammed Alnajjar, MD (A physical etching could not be obtained since the conversation happened on the web through Skype.)

